#include <ntifs.h>
#include <ntintsafe.h>
#include <windef.h>
NTSTATUS KeReadProcessMemory(PEPROCESS Process, PVOID SourceAddress, PVOID TargetAddress, SIZE_T Size)
{
PEPROCESS SourceProcess = Process;
PEPROCESS TargetProcess = PsGetCurrentProcess();
SIZE_T Result;
if (NT_SUCCESS(MmCopyVirtualMemory(SourceProcess, SourceAddress, TargetProcess, TargetAddress, Size, KernelMode, &Result)))
return STATUS_SUCCESS;
else
return STATUS_ACCESS_DENIED;
}
BOOLEAN WIN10_WriteProcessMemory(HANDLE Pid, PVOID Address, SIZE_T BYTE_size, PVOID VirtualAddress)
{
PVOID buff1;
VOID *buff2;
int MemoryNumerical = 0;
KAPC_STATE KAPC = { 0 };
PEPROCESS Process;
PsLookupProcessByProcessId((HANDLE)Pid, &Process);
__try
{
buff1 = ExAllocatePoolWithTag((POOL_TYPE)0, BYTE_size, 1997);
buff2 = buff1;
*(int*)buff1 = 1;
if (MmIsAddressValid((PVOID)VirtualAddress))
{
memcpy(buff2, VirtualAddress, BYTE_size);
}
else
{
return FALSE;
}
KeStackAttachProcess((PRKPROCESS)Process, &KAPC);
if (MmIsAddressValid((PVOID)Address))
{
ProbeForWrite(Address, BYTE_size, 1);
memcpy(Address, buff2, BYTE_size);
}
else
{
return FALSE;
}
KeUnstackDetachProcess(&KAPC);
ExFreePoolWithTag(buff2, 1997);
}
__except (EXCEPTION_EXECUTE_HANDLER)
{
return FALSE;
}
return FALSE;
}
INT64 WIN10_WriteDeviationIntMemory(HANDLE Pid, LONG Base, DWORD offset[32], DWORD len, INT64 SetValue)
{
INT64 Value = 0;
LPCVOID pbase = (LPCVOID)Base;
LPVOID rbuffer = (LPVOID)&Value;
PEPROCESS Process;
PsLookupProcessByProcessId((HANDLE)Pid, &Process);
for (int x = len - 1; x >= 0; x--)
{
__try
{
KeReadProcessMemory(Process, pbase, rbuffer, 4);
pbase = (LPCVOID)(Value + offset[x]);
}
__except (EXCEPTION_EXECUTE_HANDLER)
{
return 0;
}
}
__try
{
KeReadProcessMemory(Process, pbase, rbuffer, 4);
}
__except (EXCEPTION_EXECUTE_HANDLER)
{
return 0;
}
BOOLEAN ref = WIN10_WriteProcessMemory(Pid, (void *)pbase, 4, &SetValue);
if (ref == TRUE)
{
DbgPrint("[内核写成功] # 写入地址: %x \n", pbase);
return 1;
}
return 0;
}
VOID UnDriver(PDRIVER_OBJECT driver)
{
DbgPrint("Uninstall Driver \n");
}
NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath)
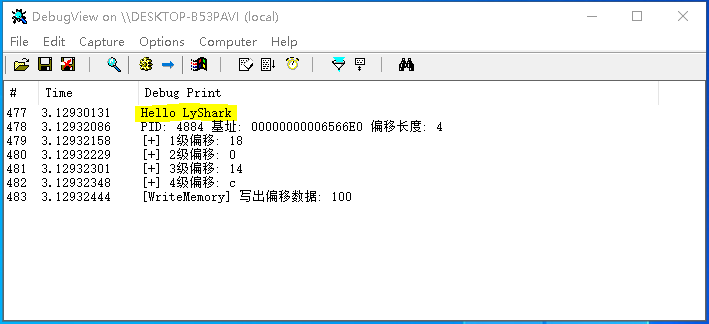
{
DbgPrint("Hello LyShark \n");
DWORD PID = 4884;
LONG PBase = 0x6566e0;
LONG Size = 4;
INT64 SetValue = 100;
DWORD Offset[32] = { 0 };
Offset[0] = 0x18;
Offset[1] = 0x0;
Offset[2] = 0x14;
Offset[3] = 0x0c;
INT64 write = WIN10_WriteDeviationIntMemory(PID, PBase, Offset, Size, SetValue);
DbgPrint("PID: %d 基址: %p 偏移长度: %d \n", PID, PBase, Size);
DbgPrint("[+] 1级偏移: %x \n", Offset[0]);
DbgPrint("[+] 2级偏移: %x \n", Offset[1]);
DbgPrint("[+] 3级偏移: %x \n", Offset[2]);
DbgPrint("[+] 4级偏移: %x \n", Offset[3]);
DbgPrint("[WriteMemory] 写出偏移数据: %d \n", SetValue);
Driver->DriverUnload = UnDriver;
return STATUS_SUCCESS;
}
|