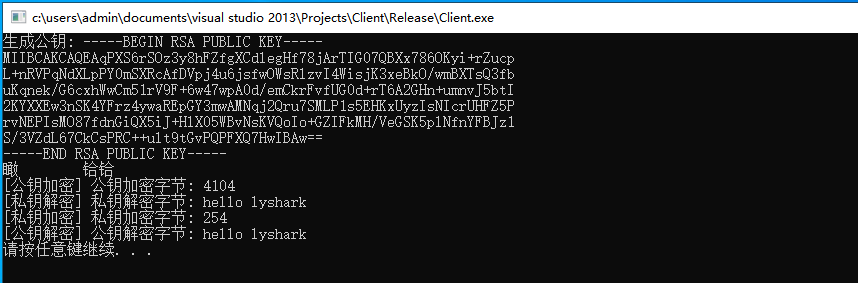
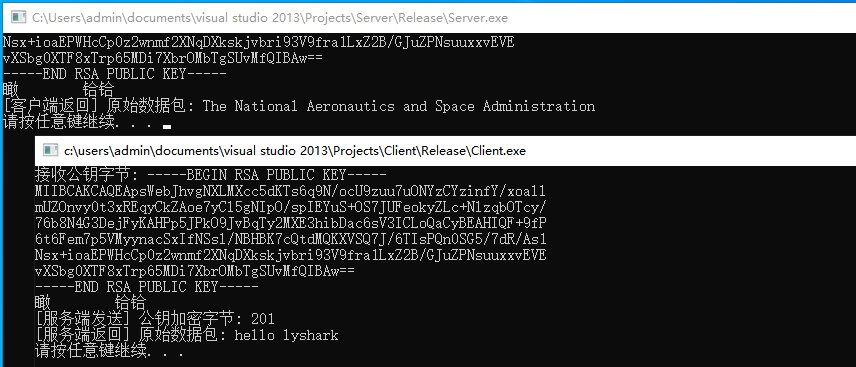
#include <iostream>
#include <Windows.h>
#include <openssl/err.h>
#include <openssl/evp.h>
#include <openssl/pem.h>
#include <openssl/rsa.h>
#include <openssl/crypto.h>
extern "C"
{
#include <openssl/applink.c>
}
#pragma comment(lib,"ws2_32.lib")
#pragma comment(lib,"libssl_static.lib")
#pragma comment(lib,"libcrypto.lib")
BOOL GenerateMemoryRSAKeys(char** private_key, char** public_key, int key_length)
{
RSA* keypair = RSA_generate_key(key_length, 3, NULL, NULL);
BIO* pri = BIO_new(BIO_s_mem());
BIO* pub = BIO_new(BIO_s_mem());
if (!PEM_write_bio_RSAPrivateKey(pri, keypair, NULL, NULL, 0, NULL, NULL))
{
return FALSE;
}
if (!PEM_write_bio_RSAPublicKey(pub, keypair))
{
return FALSE;
}
size_t pri_len = BIO_pending(pri);
size_t pub_len = BIO_pending(pub);
char* prikey = (char*)malloc(pri_len + 1);
char* pubkey = (char*)malloc(pub_len + 1);
if (prikey == NULL && pubkey == NULL)
{
return FALSE;
}
BIO_read(pri, prikey, pri_len);
BIO_read(pub, pubkey, pub_len);
*private_key = prikey;
*public_key = pubkey;
RSA_free(keypair);
BIO_free_all(pri);
BIO_free_all(pub);
return TRUE;
}
BOOL rsa_encrypt(char* pub_key, char* msg, char** encrypt, int* encrypt_len, char *type)
{
RSA* rsa = NULL;
BIO* keybio = BIO_new_mem_buf((void*)pub_key, -1);
char* err = (char*)malloc(130);
if (keybio == NULL)
{
return FALSE;
}
if (strcmp(type, "public") == 0)
{
if (!(rsa = PEM_read_bio_RSAPublicKey(keybio, NULL, NULL, NULL)))
{
return FALSE;
}
}
else if (strcmp(type, "private") == 0)
{
if (!(rsa = PEM_read_bio_RSAPrivateKey(keybio, NULL, NULL, NULL)))
{
return FALSE;
}
}
*encrypt_len = RSA_size(rsa);
*encrypt = (char*)malloc(4096);
if (strcmp(type, "public") == 0)
{
if ((RSA_public_encrypt(strlen(msg) + 1, (unsigned char*)msg, (unsigned char*)*encrypt, rsa, RSA_PKCS1_PADDING)) == -1)
{
return FALSE;
}
}
else if (strcmp(type, "private") == 0)
{
if ((RSA_private_encrypt(strlen(msg) + 1, (unsigned char*)msg, (unsigned char*)*encrypt, rsa, RSA_PKCS1_PADDING)) == -1)
{
return FALSE;
}
}
RSA_free(rsa);
free(err);
BIO_free_all(keybio);
return TRUE;
}
BOOL rsa_decrypt(char* pri_key, char* msg, char** decrypt, int encrypt_len, char *type)
{
RSA* rsa = NULL;
BIO* keybio = BIO_new_mem_buf(pri_key, -1);
if (keybio == NULL)
{
return FALSE;
}
if (strcmp(type, "public") == 0)
{
if (!(rsa = PEM_read_bio_RSAPublicKey(keybio, NULL, NULL, NULL)))
{
return FALSE;
}
}
else if (strcmp(type, "private") == 0)
{
if (!(rsa = PEM_read_bio_RSAPrivateKey(keybio, NULL, NULL, NULL)))
{
return FALSE;
}
}
char* err = (char*)malloc(130);
*decrypt = (char*)malloc(encrypt_len);
if (strcmp(type, "public") == 0)
{
if (RSA_public_decrypt(encrypt_len, (unsigned char*)msg, (unsigned char*)*decrypt, rsa, RSA_PKCS1_PADDING) == -1)
{
return FALSE;
}
}
else if (strcmp(type, "private") == 0)
{
if (RSA_private_decrypt(encrypt_len, (unsigned char*)msg, (unsigned char*)*decrypt, rsa, RSA_PKCS1_PADDING) == -1)
{
return FALSE;
}
}
RSA_free(rsa);
free(err);
BIO_free_all(keybio);
return TRUE;
}
int main(int argc, char *argv)
{
char *private_key, *public_key;
if (GenerateMemoryRSAKeys(&private_key, &public_key, 2048))
{
std::cout << "生成私钥: " << private_key << std::endl;
std::cout << "生成公钥: " << public_key << std::endl;
}
char *encrypt, *decrypt;
int encrypt_length;
BOOL flag;
flag = rsa_encrypt(public_key, (char*)"hello lyshark", &encrypt, &encrypt_length, (char *)"public");
if (flag == TRUE)
{
std::cout << "[公钥加密] 公钥加密字节: " << strlen(encrypt) << std::endl;
}
flag = rsa_decrypt(private_key, encrypt, &decrypt, encrypt_length, (char *)"private");
if (flag == TRUE)
{
std::cout << "[私钥解密] 私钥解密字节: " << decrypt << std::endl;
}
flag = rsa_encrypt(private_key, (char*)"hello lyshark", &encrypt, &encrypt_length, (char*)"private");
if (flag == TRUE)
{
std::cout << "[私钥加密] 私钥加密字节: " << strlen(encrypt) << std::endl;
}
flag = rsa_decrypt(public_key, encrypt, &decrypt, encrypt_length, (char*)"public");
if (flag == TRUE)
{
std::cout << "[公钥解密] 公钥解密字节: " << decrypt << std::endl;
}
system("pause");
return 0;
}
|