#include "lyshark_lde64.h"
#include <ntifs.h>
#include <windef.h>
#include <intrin.h>
#pragma intrinsic(_disable)
#pragma intrinsic(_enable)
typedef INT(*LDE_DISASM)(PVOID address, INT bits);
LDE_DISASM lde_disasm;
VOID lde_init()
{
lde_disasm = ExAllocatePool(NonPagedPool, 12800);
memcpy(lde_disasm, szShellCode, 12800);
}
ULONG GetFullPatchSize(PUCHAR Address)
{
ULONG LenCount = 0, Len = 0;
while (LenCount <= 14)
{
Len = lde_disasm(Address, 64);
Address = Address + Len;
LenCount = LenCount + Len;
}
return LenCount;
}
typedef NTSTATUS(__fastcall *PSLOOKUPPROCESSBYPROCESSID)(HANDLE ProcessId, PEPROCESS *Process);
ULONG64 protect_eprocess = 0;
ULONG patch_size = 0;
PUCHAR head_n_byte = NULL;
PVOID original_address = NULL;
KIRQL WPOFFx64()
{
KIRQL irql = KeRaiseIrqlToDpcLevel();
UINT64 cr0 = __readcr0();
cr0 &= 0xfffffffffffeffff;
__writecr0(cr0);
_disable();
return irql;
}
VOID WPONx64(KIRQL irql)
{
UINT64 cr0 = __readcr0();
cr0 |= 0x10000;
_enable();
__writecr0(cr0);
KeLowerIrql(irql);
}
PVOID GetProcessAddress(PCWSTR FunctionName)
{
UNICODE_STRING UniCodeFunctionName;
RtlInitUnicodeString(&UniCodeFunctionName, FunctionName);
return MmGetSystemRoutineAddress(&UniCodeFunctionName);
}
PVOID KernelHook(IN PVOID ApiAddress, IN PVOID Proxy_ApiAddress, OUT PVOID *Original_ApiAddress, OUT ULONG *PatchSize)
{
KIRQL irql;
UINT64 tmpv;
PVOID head_n_byte, ori_func;
UCHAR jmp_code[] = "\xFF\x25\x00\x00\x00\x00\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF";
UCHAR jmp_code_orifunc[] = "\xFF\x25\x00\x00\x00\x00\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF";
*PatchSize = GetFullPatchSize((PUCHAR)ApiAddress);
head_n_byte = ExAllocatePoolWithTag(NonPagedPool, *PatchSize, "LyShark");
irql = WPOFFx64();
RtlCopyMemory(head_n_byte, ApiAddress, *PatchSize);
WPONx64(irql);
ori_func = ExAllocatePoolWithTag(NonPagedPool, *PatchSize + 14, "LyShark");
RtlFillMemory(ori_func, *PatchSize + 14, 0x90);
tmpv = (ULONG64)ApiAddress + *PatchSize;
RtlCopyMemory(jmp_code_orifunc + 6, &tmpv, 8);
RtlCopyMemory((PUCHAR)ori_func, head_n_byte, *PatchSize);
RtlCopyMemory((PUCHAR)ori_func + *PatchSize, jmp_code_orifunc, 14);
*Original_ApiAddress = ori_func;
tmpv = (UINT64)Proxy_ApiAddress;
RtlCopyMemory(jmp_code + 6, &tmpv, 8);
irql = WPOFFx64();
RtlFillMemory(ApiAddress, *PatchSize, 0x90);
RtlCopyMemory(ApiAddress, jmp_code, 14);
WPONx64(irql);
return head_n_byte;
}
VOID KernelUnHook(IN PVOID ApiAddress, IN PVOID OriCode, IN ULONG PatchSize)
{
KIRQL irql;
irql = WPOFFx64();
RtlCopyMemory(ApiAddress, OriCode, PatchSize);
WPONx64(irql);
}
NTSTATUS MyPsLookupProcessByProcessId(HANDLE ProcessId, PEPROCESS *Process)
{
NTSTATUS st;
st = ((PSLOOKUPPROCESSBYPROCESSID)original_address)(ProcessId, Process);
if (NT_SUCCESS(st))
{
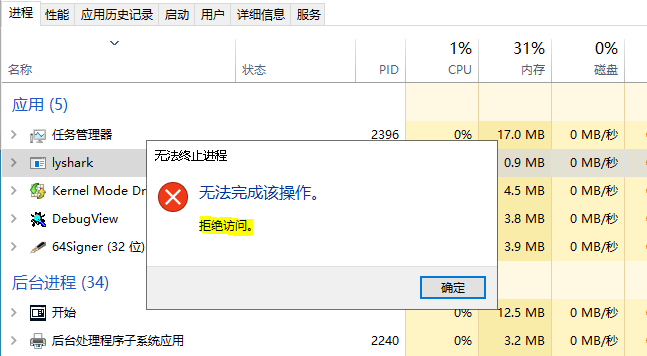
if (*Process == (PEPROCESS)protect_eprocess)
{
*Process = 0;
DbgPrint("[lyshark] 拦截结束进程 \n");
st = STATUS_ACCESS_DENIED;
}
}
return st;
}
VOID UnDriver(PDRIVER_OBJECT driver)
{
DbgPrint("驱动已卸载 \n");
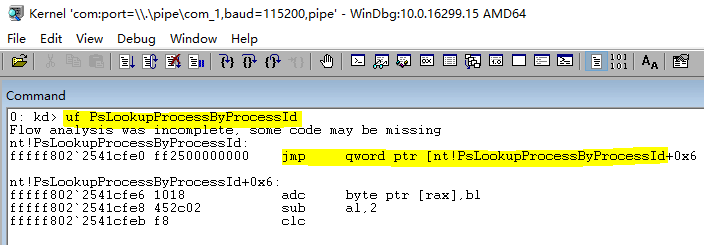
KernelUnHook(GetProcessAddress(L"PsLookupProcessByProcessId"), head_n_byte, patch_size);
}
NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath)
{
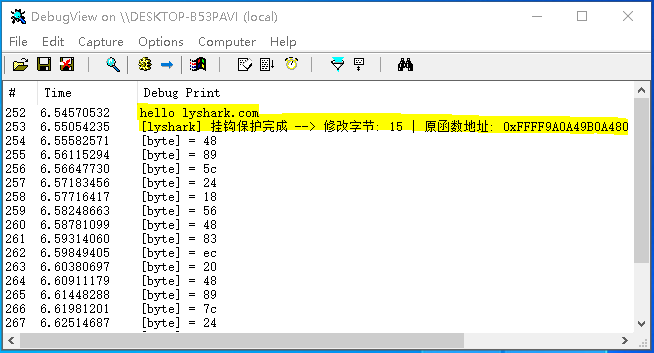
DbgPrint("hello lyshark.com \n");
lde_init();
protect_eprocess = 0xffff9a0a44ec4080;
head_n_byte = KernelHook(GetProcessAddress(L"PsLookupProcessByProcessId"), (PVOID)MyPsLookupProcessByProcessId, &original_address, &patch_size);
DbgPrint("[lyshark] 挂钩保护完成 --> 修改字节: %d | 原函数地址: 0x%p \n", patch_size, original_address);
for (size_t i = 0; i < patch_size; i++)
{
DbgPrint("[byte] = %x", head_n_byte[i]);
}
Driver->DriverUnload = UnDriver;
return STATUS_SUCCESS;
}
|